The rapid evolution of enterprise computing, driven by cloud migration, remote work proliferation, and the decentralization of infrastructure, has significantly expanded the attack surface for cyber adversaries. Legacy security models predicated on implicit trust within a network perimeter have proven inadequate in countering sophisticated and persistent threats. Zero Trust Architecture (ZTA) fundamentally disrupts this paradigm by adhering to three cardinal principles:
- Never Trust, Always Verify: Security validation is a continuous process, wherein every entity — human or machine — must be authenticated and authorized dynamically.
- Implement Least Privilege: Access control policies enforce minimal necessary permissions, mitigating potential damage from compromised credentials or insider threats.
- Assume Breach: Organizations operate under the presumption of inevitable compromise, ensuring robust detection, response, and containment mechanisms are in place.
By rigorously verifying every request in real-time, Zero Trust ensures that security policies remain adaptive and contextually aware, rather than relying on static perimeter-based defenses.
Why Traditional Security Falls Short

Traditional security architectures, such as firewalls, VPNs, and static access controls, predominantly follow a “trust but verify” approach. However, once an adversary infiltrates the network perimeter, they often gain unrestricted lateral movement, which exposes critical resources. The following systemic weaknesses of traditional models can be exploited:
- Insider Threats: Malicious or negligent actors within an organization can misuse privileges to exfiltrate sensitive data.
- Credential Compromise: Stolen or forged credentials can be leveraged to access critical systems without triggering alarms.
- Remote Work and BYOD Risks: Personal devices and external networks introduce new vectors for infiltration.
- Expanding Attack Surfaces: The adoption of cloud-native services, IoT, and distributed infrastructures necessitates more dynamic security models.
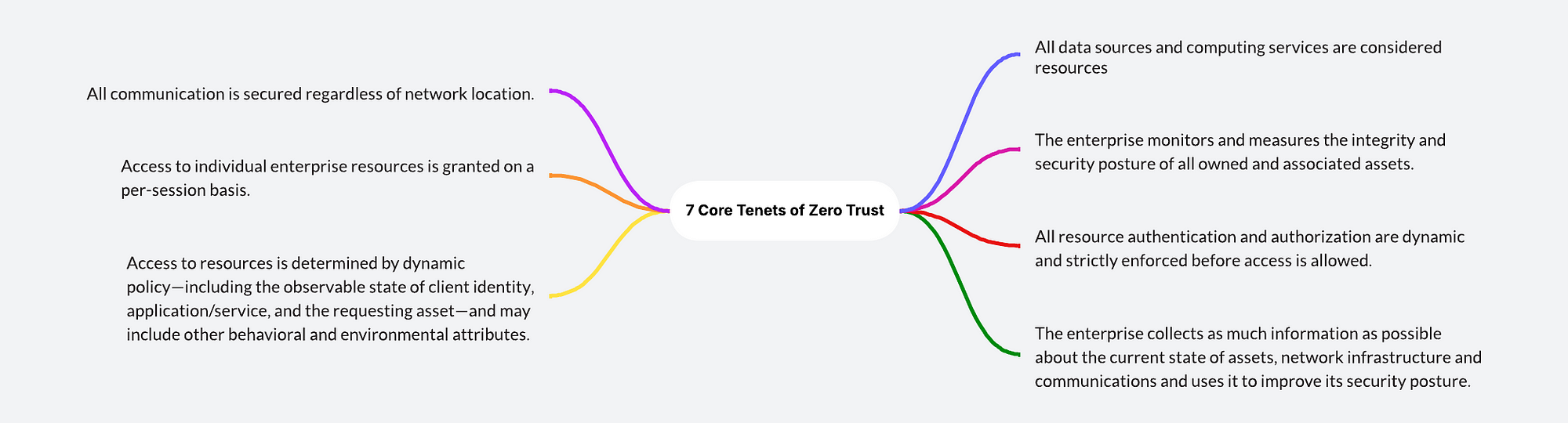
Zero Trust Framework — 7 Core Tenets and Basic Components
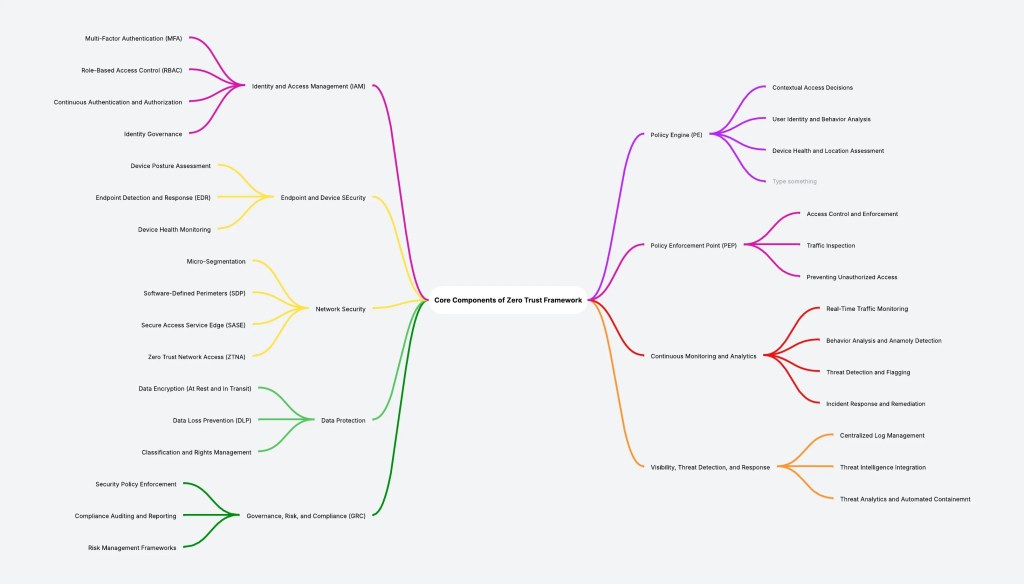
Zero Trust is a transformative security philosophy that addresses the shortcomings of traditional models. Its core tenets — least privilege, microsegmentation, continuous verification, and an ‘assume breach’ mindset — ensure that every access request is rigorously validated, minimizing attack surfaces and limiting breach impact. By embedding real-time monitoring and adaptive security policies, Zero Trust enhances threat detection and response. Effective implementation requires a framework built on identity, context, and continuous verification, forming the foundation for a resilient security posture. The core Tenets and components of Zero Trust are as depicted below:
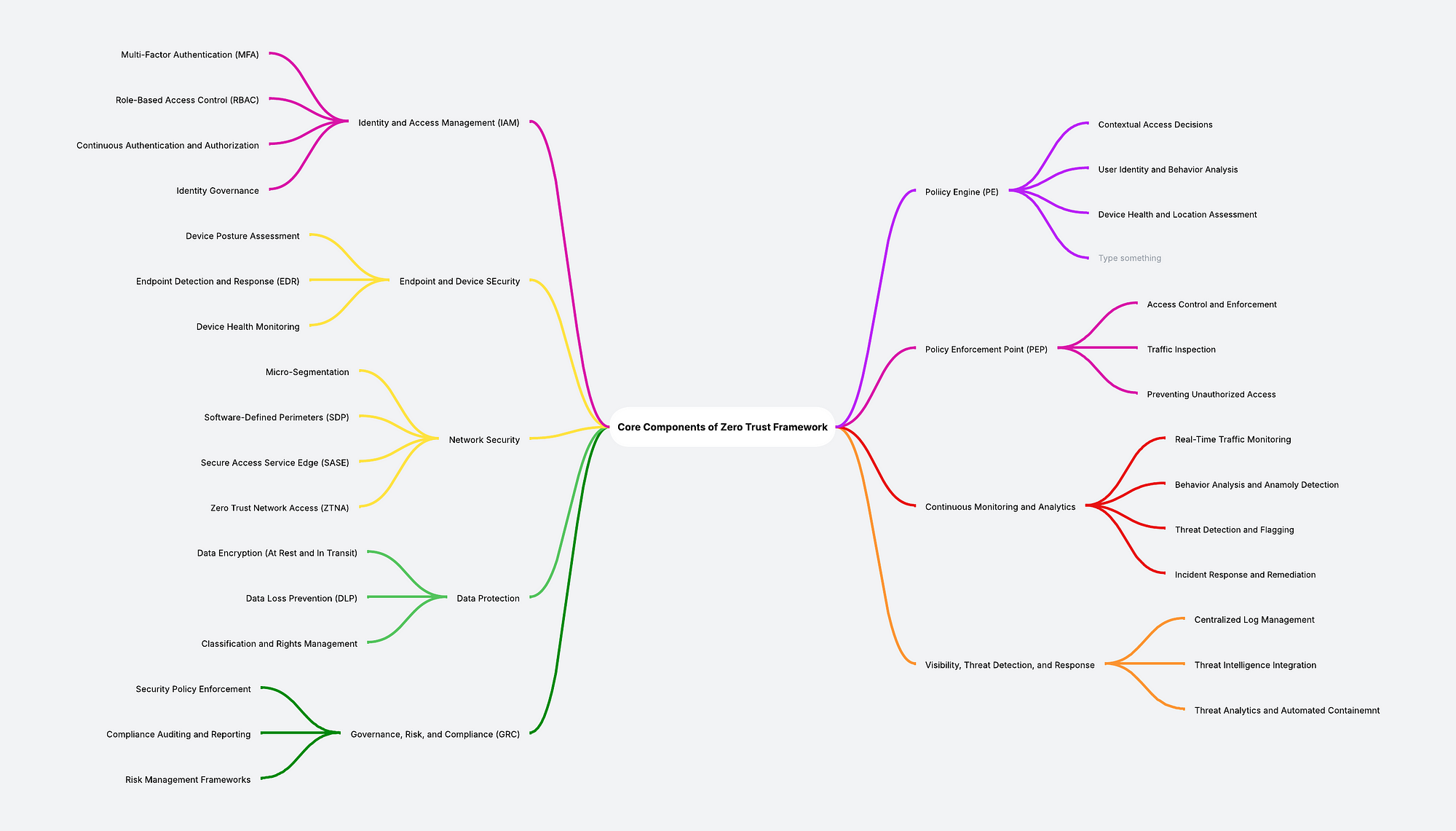
Policy Engine (PE)
- Evaluates access requests dynamically based on contextual factors.
- Assesses user identity, device health, location, and behavior patterns.
- Determines whether to grant, deny, or challenge access requests.
Policy Enforcement Point (PEP)
- Acts as the enforcement mechanism for access control decisions.
- Implements security policies by allowing or blocking requests.
- Inspects incoming traffic to prevent unauthorized access and lateral movement.
Continuous Monitoring and Analytics
- Provides real-time surveillance of network activity and user behavior.
- Leverages AI-driven analytics to detect anomalies and potential threats.
- Flags suspicious activity for immediate investigation and response.
- Ensures continuous validation beyond initial authentication.
Identity and Access Management (IAM)
- Authenticates users and devices before granting access.
- Enforces Multi-Factor Authentication (MFA) for enhanced security.
- Implements Role-Based Access Control (RBAC) and adaptive access policies.
- Manages identity governance, ensuring proper lifecycle and permission oversight.
Endpoint and Device Security
- Conducts device posture assessments to enforce security compliance.
- Continuously monitors device health for vulnerabilities and risks.
- Deploys Endpoint Detection and Response (EDR) to detect and mitigate threats.
- Implements Zero Trust Network Access (ZTNA) to verify device trustworthiness.
Network Security
- Restricts unauthorized movement through microsegmentation.
- Implements Software-Defined Perimeters (SDP) for controlled access.
- Integrates Secure Access Service Edge (SASE) for security-driven networking.
- Enforces Zero Trust Network Access (ZTNA) to validate all connections.
Data Protection
- Encrypts data at rest and in transit to ensure confidentiality.
- Implements Data Loss Prevention (DLP) strategies to prevent unauthorized exfiltration.
- Applies data classification and rights management to regulate access and control sharing.
Visibility, Threat Detection, and Response
- Maintains centralized log management for comprehensive security oversight.
- Integrates real-time threat intelligence for proactive defense.
- Utilizes AI-driven analytics to identify and assess suspicious activities.
- Automates incident response and containment measures to mitigate risks.
Governance, Risk, and Compliance (GRC)
- Enforces standardized security policies to ensure organizational compliance.
- Aligns with regulatory requirements across industries and jurisdictions.
- Establishes risk management frameworks to identify and mitigate potential vulnerabilities.
Implementing Zero Trust
Zero Trust is a journey, not a one-time project. Organizations should implement ZTA incrementally to minimize disruption and build confidence across teams. Here’s a structured approach to guide the process:

Step 1: Visualize — Gain Full Visibility
- Identify and map all resources, endpoints, applications, and users.
- Maintain real-time asset inventory.
- Categorize data based on sensitivity.
- Understand user access patterns.
Step 2: Mitigate — Apply Security Controls
- Enforce least privilege access.
- Implement microsegmentation.
- Utilize behavioral analytics for anomaly detection.
Step 3: Optimize — Refine and Expand
- Automate policy enforcement using AI-driven tools.
- Extend Zero Trust to multi-cloud and hybrid environments.
- Integrate with DevSecOps to embed security in development pipelines.
Challenges in Zero Trust Adoption
Organizations may face several challenges when transitioning to Zero Trust:
- Architectural Overhaul: Requires significant changes to IT infrastructure.
- Legacy Compatibility: Older systems may not integrate easily with Zero Trust.
- Increased Friction: Frequent authentication can impact user experience.
- High Costs and Resources: Requires investment in new technologies and staff training.
- Dynamic Policy Management: Continuous updates and enforcement can be complex.
Key Benefits of Zero Trust Architecture
By embedding rigorous access controls and monitoring across all layers, Zero Trust provides:
- Simplified Security Management: Automates security processes and consolidates tools.
- Reduced Attack Surface: Enforces least privilege and network segmentation.
- Enhanced Visibility and Control: Monitors user behavior, endpoint health, and network traffic.
- Compliance and Risk Mitigation: Aligns with regulatory requirements.
- Cost Efficiency: Reduces reliance on hardware-based perimeter defenses.
Overcoming Adoption Challenges
To ease the transition:
- Start Small: Implement Zero Trust on high-value assets first.
- Engage Stakeholders: Communicate benefits to gain organizational buy-in.
- Invest in Automation: Utilize AI-driven policy enforcement to scale efficiently.
Zero Trust Architecture is more than an evolution — it’s a cybersecurity revolution. As threats become increasingly dynamic, traditional models no longer suffice. Zero Trust’s continuous verification, least privilege access, and microsegmentation form a resilient defense that protects critical assets, minimizes breach impacts, and strengthens compliance.
This paradigm is a strategic imperative, not just a technological upgrade. By starting small and iterating quickly, organizations can adapt to evolving threats and secure a robust digital future.
References & Further Reading:
How To Implement Zero Trust Architecture (Reduce Security Risks)
Get a comprehensive view of the Zero Trust Model and what powers it to effectively scale and secure your cloud…
Zero Trust Architecture – System Design – GeeksforGeeks
https://www.microsoft.com/en-us/security/business/zero-trust
https://www.zscaler.com/resources/security-terms-glossary/what-is-zero-trust-architecture